This article applies to PRTG Network Monitor 14 or later
Separating Ingress and Egress Traffic
To separate the ingress and egress traffic on a port, set up a flow sensor for each interface. Particularly define an Include Filter for each sensor:
InboundInterface[interface-number]
-or-
OutboundInterface[interface_number]
Note: The interface number must be the interface number that appears inside the flow, which is not the same as the interface number that appears in the CLI (Command Line Interface) of the switch.
The interface_number can only be a single integer number, with no alphabet or special characters. So, you must use a number like “12” rather than “gi0/0/10”.
The interface numbers that appear inside the flow are not standardized and differ from model to model, also between models from the same vendor. They are often the same or similar to the interface index numbers that appear in SNMP counters, but this cannot be guaranteed.
How to Find Out the Interface Numbers
You have two options to determine the interface numbers for your model, either via the log file of a NetFlow sensor, or with the NetFlow Tester.
Finding Out Interface Numbers with the NetFlow Tester (V9/IPFIX ONLY)
You can use our free NetFlow Tester to get the correct interface numbers. Follow the instructions on the NetFlow Tester page to get flow data with the tool and analyze the Decoded Flows section. Find the interface numbers for inbound and outbound traffic next to the IF/OF entry (in the screenshot below, these are "3" and "2" for common flows, and "65535" internal traffic).
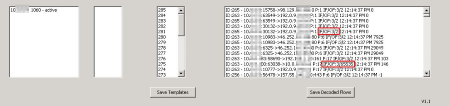
Click here to enlarge.
Finding Out Interface Numbers with the Log File
- Set up a flow sensor, with no filtering, so that it includes all flows.
- In the sensor settings, enable Log Stream Data to Disk, and select the option All Stream Data.
- Run the logging long enough to be sure that you have both ingress and egress traffic on the interface captured in the log file.
- Disable the logging again, because stream logging can generate very large files on your PRTG server.
- You can find the resulting stream log file in the \StreamLog subfolder of your PRTG data folder.
- Open the log file and search for traffic that you know was ingress or egress on the interface you are interested in.
- Use the numbers in the columns InboundInterface and OutboundInterface in the include filter of your flow sensors.
Filtering over IP Ranges
Depending on the configuration of your router, inbound and outbound interfaces might not be useful for your use case. An alternative approach to this would be to filter over IP ranges.
Usually, internal IP addresses can be identified easily by filtering with a hostmask. Then you can create filters accordingly, for example inbound:
(not sourceip[<intern_ip_range>]) and destinationip[<intern_ip_range>]
The filter for outbound would then be vice versa.

Add comment