I want to use Okta as SSO provider to authenticate users in PRTG. How can I do this? What configuration steps are necessary?
13 Replies
Votes:
0
This article applies as of PRTG 22.x.76
| Important notice: The following article only applies to PRTG Network Monitor. It does not apply to PRTG Hosted Monitor. |
How to integrate Okta SSO into PRTG
As of PRTG 22.x.76, you can use Okta as single sign-on (SSO) provider in PRTG. For the integration to work seamlessly, follow the steps in this article.
Requirements
- PRTG as of version 22.x.76
- The optional Okta add-on API Access Management.
Configuration steps to take:
- Step 1: Configure Okta
- Step 2: Configure SSO in PRTG
- Step 3: Add a user group in PRTG
Step 1: Configure Okta
Follow these steps to configure Okta to work as SSO provider in PRTG.
- Optional steps
- Add persons (optional)
- Add groups (optional)
- Step 1.1: Add an authorization server
- Step 1.2: Create an app integration
Optional steps
Add persons (optional)
Follow the steps below to add or import persons that should have access via SSO.
- Log in to the Okta administrator console under https://${yourOktaDomain}/admin/dashboard.
- Go to Directory | People.
- Choose between Add person to add persons manually and Import users from CSV to import persons from a .csv file.
- If you want to manually add users, see Add users manually | Okta.
- If you want to use a .csv file to import users, see Import users from a CSV file | Okta.
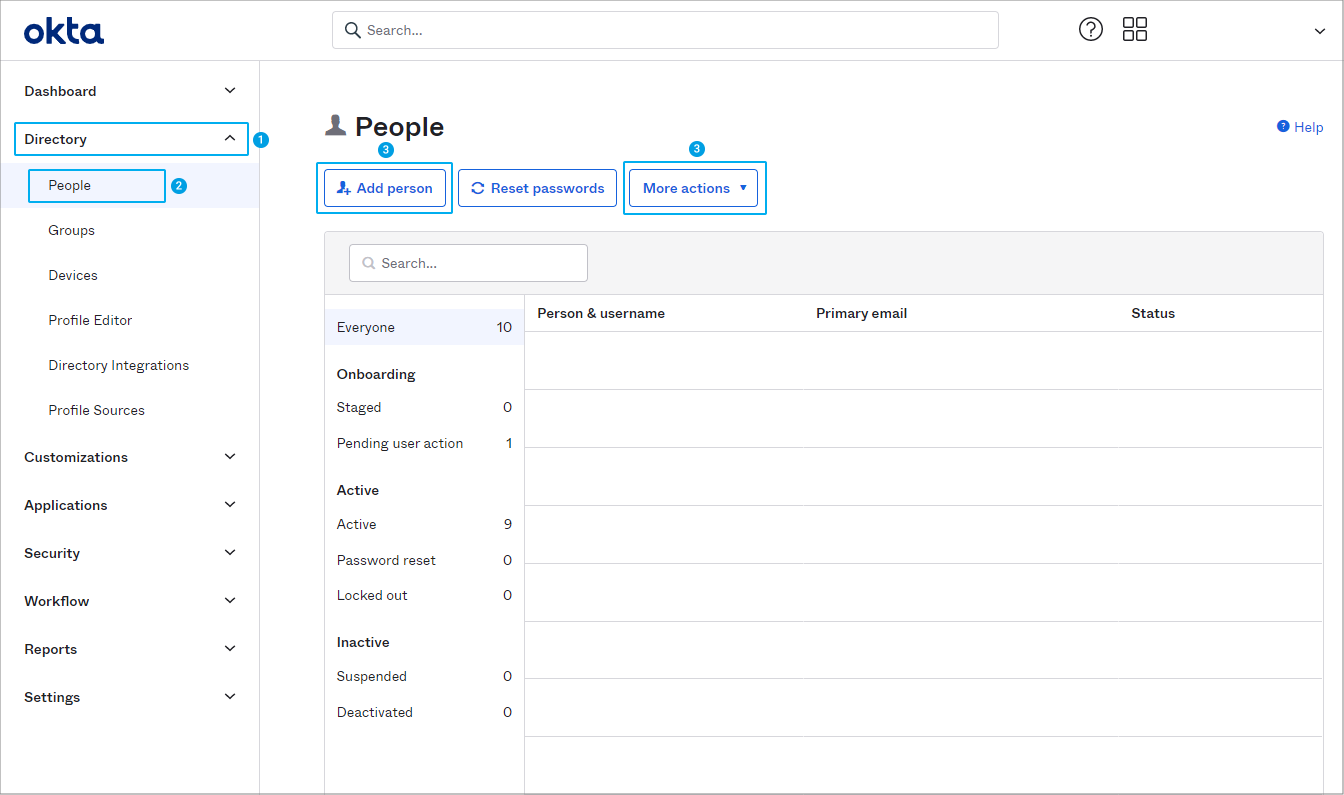
Click to enlarge - After you have successfully added the user accounts, make sure to activate them. For more information, see Activate user accounts | Okta.
For more information, see Manage users | Okta.
Add a group (optional)
Follow the steps below to add a group.
Notes:
- Add this group to the claim in step 1.1, allow it to access the application that you create in step 1.2, and add its name as SSO Group Claim in step 3 to only allow persons in this group to access your PRTG installation.
- By default, Okta creates the group Everyone that includes every person that is created on Okta. You can use Everyone as SSO Group Claim in step 3 if you want to allow all persons to access your PRTG installation.
- Log in to the Okta administrator console under https://${yourOktaDomain}/admin/dashboard.
- Go to Directory | Groups and click Add Group.
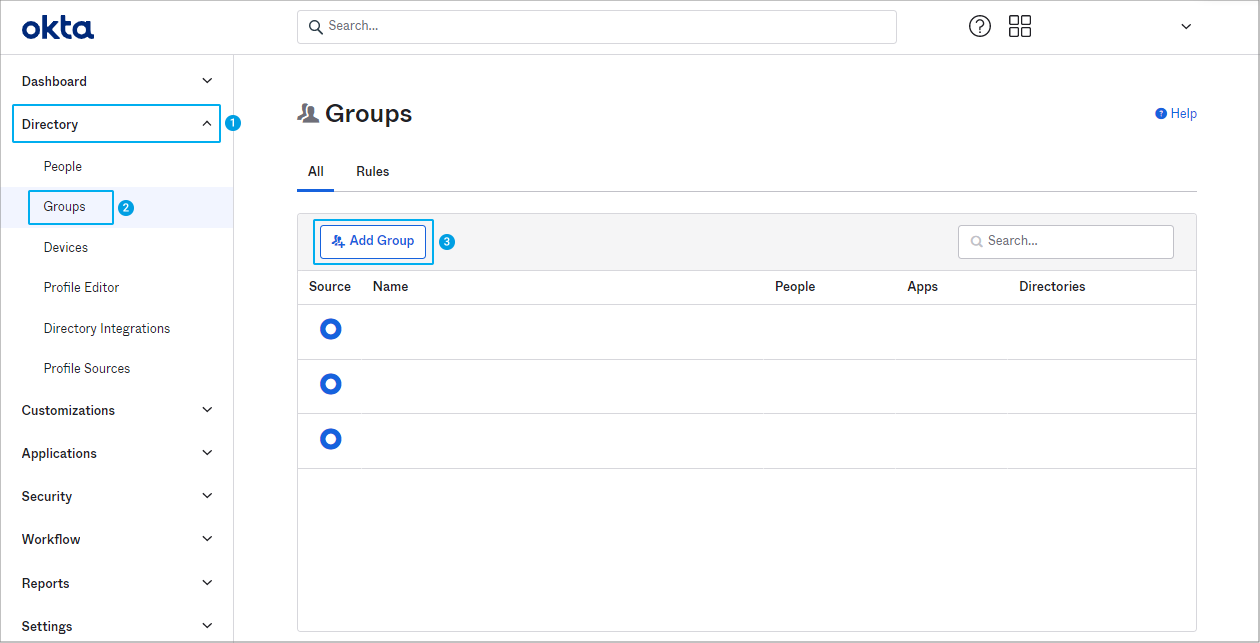
Click to enlarge - Enter a name for your group, for example My_Group.
- Click Save.
- Click Assign People.
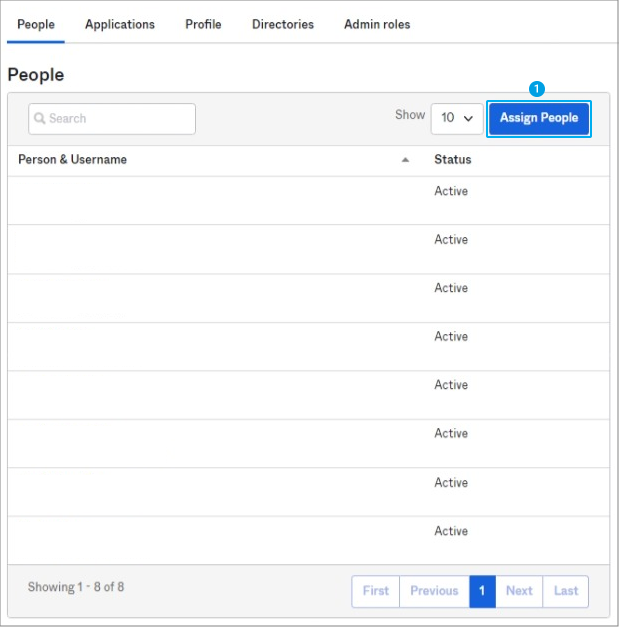
Click to enlarge - Add the members that should be in the newly created group.
- Click Save.
For more information, see Manage groups | Okta.
Step 1.1: Add an authorization server configuration
- Log in to the Okta administrator console under https://${yourOktaDomain}/admin/dashboard.
- Go to Security | API and click Add Authorization Server.
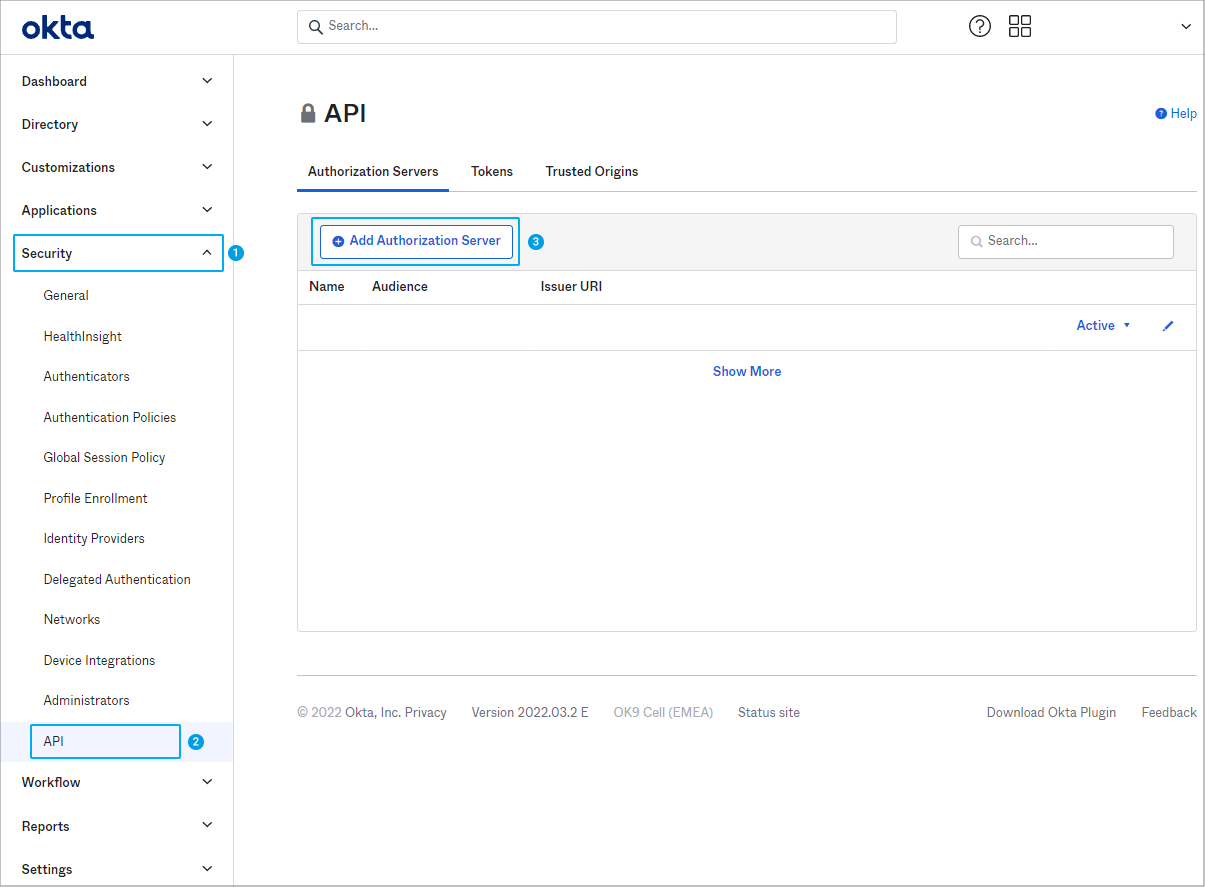
Click to enlarge - Enter a Name, for example default, and an Audience.
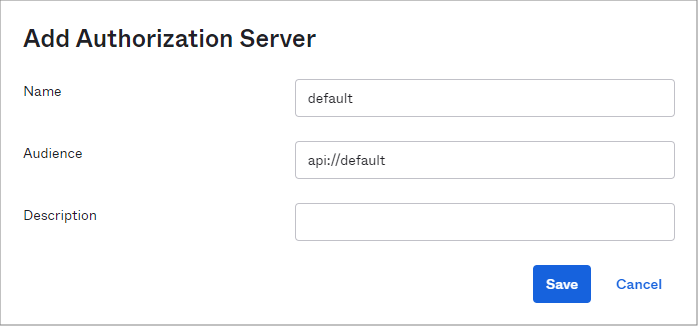
Click to enlarge - Click Save.
- Select the authorization server that you have created and navigate to tab Claims.
- Click Add Claim and enter the following values:
- Name: Enter a name, for example groups. Note: The name must be in lowercase for the login with SSO to work properly.
- Include in token type: ID Tokens – Always
- Value type: Groups
- Filter: Define a filter that defines which groups will be added to the claim of the token for this authorization server.
Note: Select Matches regex and enter .* to add all available groups to the claim.
Note: If you want to limit the groups, define the conditions to only add specific groups to the claim of the token. For example, select Equals and enter My_Group to add the group that you created during the optional step above to the claim of the token. - Disable claim: Deselected
- Include in: Any scope
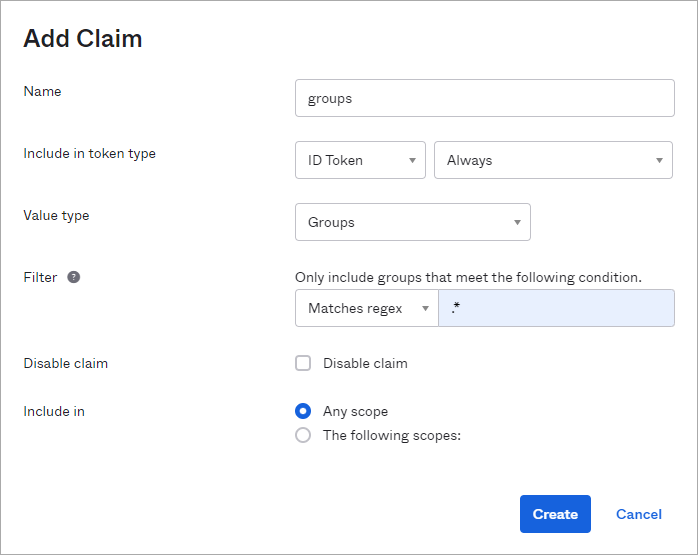
Click to enlarge - Click Create.
For more information, see Build Custom Authorization Servers for API Access Management | Okta.
Step 1.2: Create an app integration
- Go to Applications | Applications and click Create App Integration.
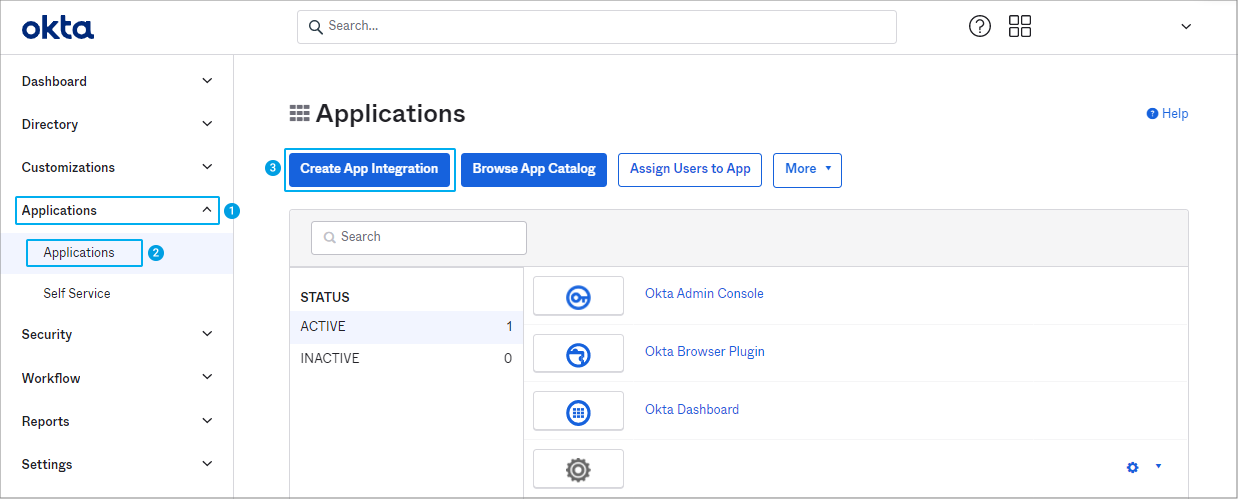 Click to enlarge.
Click to enlarge.
- Select the following settings in the window that opens:
- Sign-in method: OIDC – OpenID Connect
- Application type: Web Application
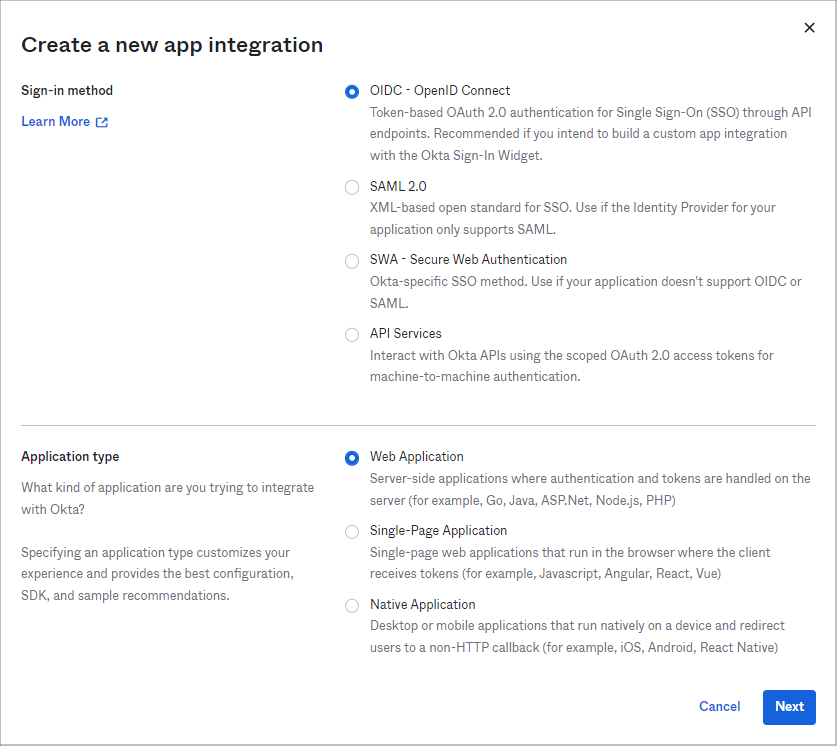
Click to enlarge
- Click Next.
- On the New Web App Integration tab, enter the following:
- Enter an App integration name, for example My Web Application.
- For Grant type, select Authorization Code and Refresh Token.
- For Sign-in redirect URIs, enter the IP addresses and DNS names of the PRTG installation(s) that your users use to connect to PRTG. For example, https://myprtg.domain.com:443/cb for the classic PRTG interface or https://\{yourserver}:1616/authorize/okta/cb for the new PRTG interface.
Note: You can also skip this step for now and add the URLs in step 2 two when you configure SSO in PRTG. - For Controlled access, select Allow everyone in your organization to access.
Note: If you select Limit access to selected groups, enter the name of the group(s) that you want to grant access. For example, add My_Group to allow the persons in the group that you created during the optional step above to access the app integration.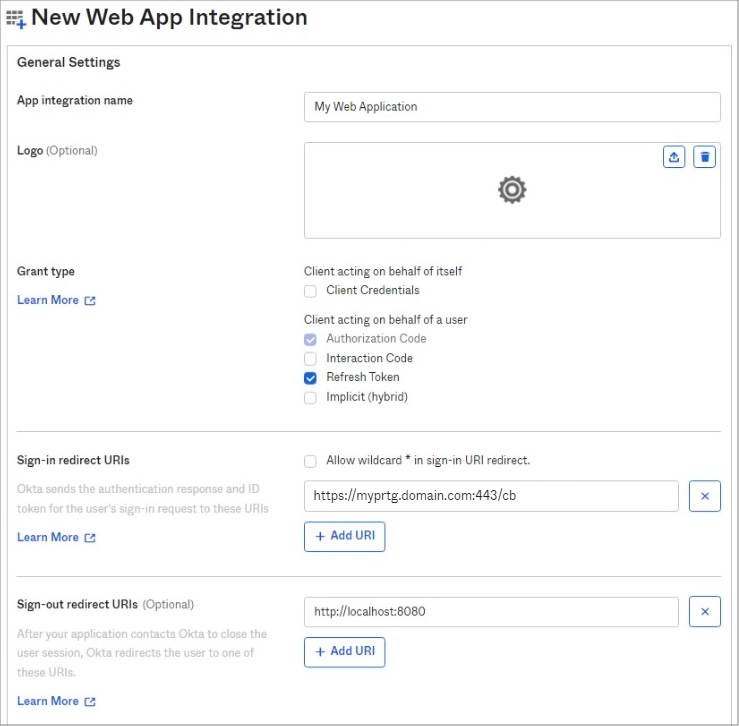 Click to enlarge
Click to enlarge
- Click Save.
Step 2: Configure SSO in PRTG
Note: When you configure SSO for the first time, you must restart the application server for SSO to work.
Now that you have configured Okta, you now need to configure the SSO settings in PRTG accordingly. To do so, follow these steps.
- Log in to the PRTG web interface.
- Go to Setup | System Administration | Single Sign-On.
- Under SSO Login, select Enable.
- Under Provider, select Okta from the dropdown list.
- Under Configuration Endpoint, enter the configuration endpoint URL as follows https://${yourOktaDomain}/oauth2/${authorizationServerId}/.well-known/oauth-authorization-server
Note: Make sure to enter the Metadata URI that you can find under Security | API | <Your Authorization Server> in the Okta administrator console. - Click Load Configuration. This automatically fills in the values in the next four fields.
Note: If this does not work, you must manually enter the values instead as follows. Also, make sure to replace ${yourOktaDomain} with the Okta domain of your application from the Okta administrator console and ${authorizationServerId} with your authorization server ID.- Authorization Endpoint: https://${yourOktaDomain}/oauth2/${authorizationServerId}/v1/authorize
- Token Endpoint: https://${yourOktaDomain}/oauth2/${authorizationServerId}/v1/token
- JSON Web Key Set (JWKS) URI: https://${yourOktaDomain}/oauth2/${authorizationServerId}/v1/keys
- Issuer: https://${yourOktaDomain}/oauth2/${authorizationServerId}
- Under Scope, enter openid offline_access email profile. The required scopes are added by default after you add your authorization server. You can find the scopes of your authorization server under Security | API | <Your Authorization Server> in the Okta administrator console.
- Under Application (Client) ID, enter the Client ID that you can find under Applications | Applications | <Your Application>.
- Under Client Secret, enter the client secret that you can also find under Applications | Applications | <Your Application>.
- Under Available Callback URLs, select the URLs that your users will use to log in to PRTG.
Here is an example what the URLs should look like: https://myprtg.domain.com:443/cb. You will need to add these to the Sign-in redirect URIs under Applications | Applications | <Your Application> in section Login in the Okta administrator console. - If the URL your users use to log in to PRTG is not listed because PRTG is reachable via a different URL (for example, myPRTG.example.com for login but PRTG lists myPRTG.internal.example.com), you can use the option Manually enter a URL. PRTG still lists all available endpoints if needed for forwarding. You then need to add the URL to the Sign-in redirect URIs under Applications | Applications | <Your Application> in section Login in the Okta administrator console.
Note: Okta and PRTG both check if the callback URLs are allowed. Make sure you configure each required URL on both ends; otherwise, you will not be able to log in. - Click Test Single Sign-On Authorization Endpoint and wait for the success message.
Note: Make sure that you have opened the PRTG installation for which you want to test the single sign-on authorization endpoint via a URL that you have configured as a valid redirection URI in the Okta administrator console.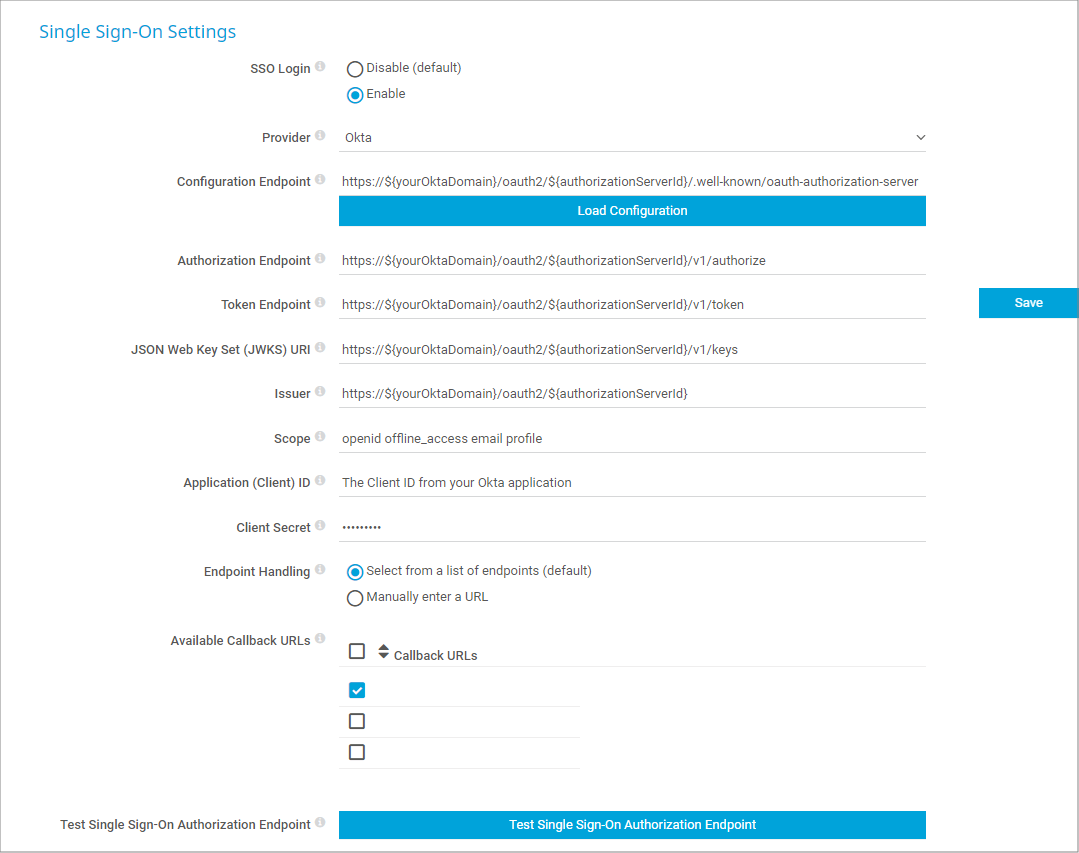
Click to enlarge - Click Save.
You have now configured SSO in PRTG.
Step 3: Add a user group in PRTG
Now that you have configured SSO, you need to add a new user group in PRTG.
| Note: A local user account for an SSO user is only created if this SSO user has successfully logged in to PRTG. |
- Log in to the PRTG web interface.
- Go to Setup | System Administration | User Groups.
- Hover over the blue (+) button and select Add User Group.
- Under User Group Name, enter a name to identify the group, for example Okta SSO User Group.
- Under Active Directory or Single Sign-On Integration, select Use single sign-on integration.
- Under SSO Group Claim, enter the access claim for the SSO group. Enter the name of the group that you want to grant access to your PRTG installation, for example My_Group.
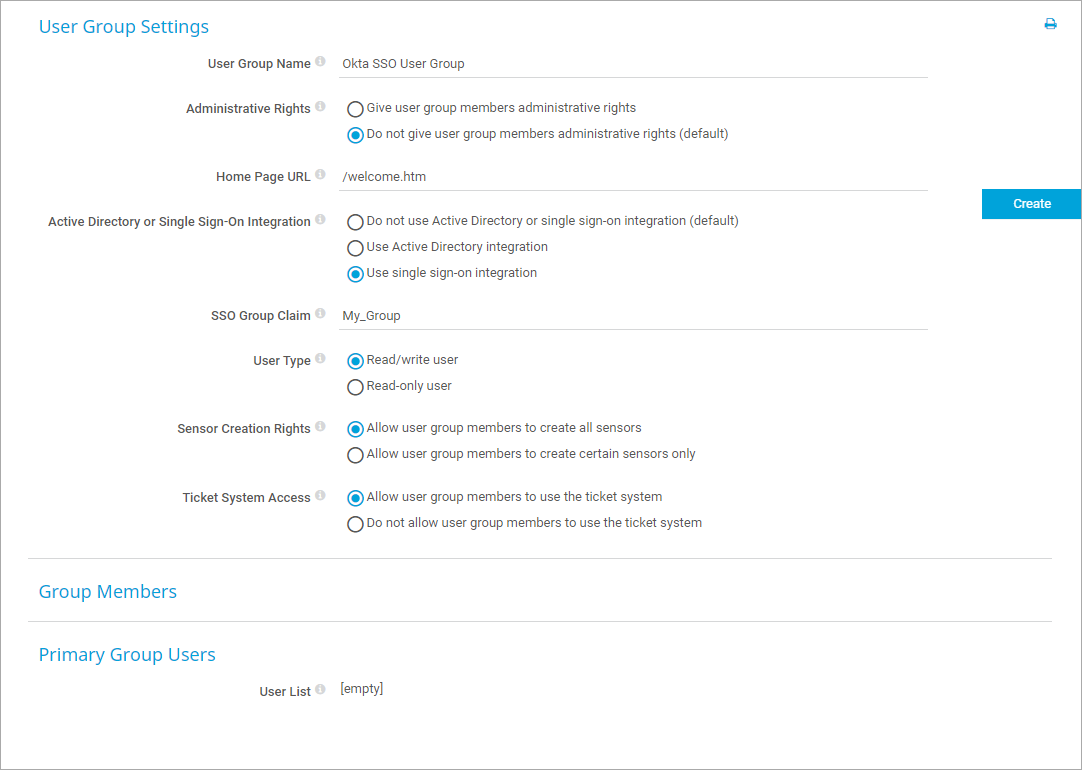
Click to enlarge - Click Create.
You have now successfully integrated Okta as SSO provider in PRTG.
Created on Apr 5, 2022 9:44:19 AM
Last change on Mar 19, 2025 9:35:42 AM by
Jacqueline Conforti [Paessler Support]
Votes:
0
Disappointing that the API Access management is required from the Okta side. Why is a custom authorization server needed? Why not use the default?
Votes:
0
Hello,
the custom server is more secure, this is why we use it here.
Votes:
1
These steps are a provide a good amount of detail, but are difficult to follow and understand. While I am familiar with Okta, I am not familiar with the process of creating a custom authorization server, and have not been able to get this to work.
I don't understand what should be used in Step 3 in the SSO Group Claim field. In the example above, the literal word example is being used. But, example is not assigned to any of the objects created in the previous steps. Can anything be put in this field? Or, should it refer to a previously created object?
A few more questions...
- In Step 1.1, the Add Claim section, the filter allows us to filter by groups. Also, in Step 1.4, the Controlled access section allows us to Limit access to selected groups. Is it best practice, in Step 1.1 to filter on a larger set of groups, or all groups. Then further refine it to a specific group in the Controlled access section? How do we add multiple groups?
- If I've done this correctly, should I expect the PRTG group to populate with user names from an Okta group?
Votes:
0
Hello,
about the group claim, you can get it this way, and add further groups via yourOktaDomain/admin/groups
Users are not synced from the whole directory, instead if a user tries to log in and the user is not yet known to PRTG, it gets authenticated with querying Okta and if that passes, the user is created in PRTG and added to the SSO group.
Votes:
0
We noticed when setting the Step 1.1: Add an authorization server configuration, when doing the Add Claim part, the Name section had to be all in lowercase - "groups". Otherwise if it was "Groups" as it is in the screenshot it would fail with errors.
Votes:
0
Hello chelliwell,
you are right. We are checking this. For now, only lower-case works.
Votes:
0
We're unable to follow these steps as we can't add the custom auth server in step 1.1 without incurring additional costs (it is, after all, an optional plugin). Is there a way we can use the built-in organization authentication server at: https://${yourOktaDomian}/.well-known/openid-configuration ?
Votes:
0
Hello fbisgaard,
I am afraid that it's not possible as PRTG needs that optional addon/plugin to perform SSO.
Votes:
0
This is an oversight by Paessler. Most Okta Workforce tenants do not have the custom API add-on. You can easily set up this integration with using the default authorization server just as hundreds of other companies do.
Votes:
0
Hello, thank you for the doc. Is there a way to prevent the need to go to the index page and click on the "Log in with single sign-on" button? And being automatically logged from Okta part?
Votes:
0
Does this integration work with the PRTG iOS App as well?
Votes:
0
Hello Fabrice,
You are welcome, as far as I am aware it's not possible.
Hello basti9,
Currently, Azure and Okta are not supported on mobile apps.
Created on Jan 27, 2023 12:06:37 PM by
Himanshu Bhatt [Paessler Support]
Last change on Jan 27, 2023 12:08:14 PM by
Himanshu Bhatt [Paessler Support]
Add comment