I want to use Microsoft Entra ID (previously Azure Active Directory or Azure AD) as SSO provider for PRTG Hosted Monitor. How can I do this? What steps are necessary?
1 Reply
Votes:
0
This article applies as of PRTG 23.x.88
| Important notice: The following article only applies to Paessler PRTG Hosted Monitor. It does not apply to PRTG Network Monitor. |
How to integrate Microsoft Entra ID into PRTG Hosted Monitor
As of PRTG 23.x.88, you can use Microsoft Entra ID as single sign-on (SSO) provider in PRTG Hosted Monitor. For the integration to work seamlessly, follow the steps in this article.
Note: PRTG app for desktop and the PRTG mobile apps do not support authentication via Entra ID.
Follow these steps to configure Microsoft Entra ID to work as SSO provider in PRTG Hosted Monitor.
- Step 1: Register your app
- Step 2: Create a client secret
- Step 3: Connect your PRTG instance to Microsoft Entra ID
- Step 4: Invite other users
Step 1: Register your app
- Log in to the Azure Portal under https://portal.azure.com.
- Select Microsoft Entra ID under Azure services.
- Go to the App registrations tab.
 Click to enlarge.
Click to enlarge.
- Click the New registration button.
- Enter a name, for example, Test.
- Select Accounts in this organizational directory only.
- Enter the redirect URI as https://auth.my-prtg.com/login/callback
 Click to enlarge.
Click to enlarge.
- Click the Register button to register the new app.
- Select the newly registered app Test.
- Copy the Application (client) ID.
Note: You will need these later to configure PRTG. Click to enlarge.
Click to enlarge.
Step 2: Create a client secret
- Go to the Certificates & secrets tab.
 Click to enlarge.
Click to enlarge.
- Click the New client secret button.

Click to enlarge.
- Enter a Description, for example, Test.
- Enter the period after which the client secret expires.
- Click the Add button to save the client secret.
- Copy and save the newly created value from the Value section as shown below:

Click to enlarge.
| Important notice: Make sure to note the client secret value now because it will not be visible again and you will need it when you configure PRTG. |
Step 3: Connect your PRTG instance to Microsoft Entra ID
- Now open the PRTG Hosted Monitor Login page.
- Go to Select your PRTG subscription.
 Click to enlarge.
Click to enlarge.
- Now take the Application (client) ID and the Client Secret and paste it in the form. Also enter the Microsoft Entra ID Domain (aka 'Primary Domain' shown in the overview page of your Entra ID tenant) and your Email domain. PRTG Hosted Monitor supports multiple emails domains as comma-separated entries as long as they are under the same tenant.
- Confirm by clicking on Create.
- Now PRTG will restart and prepare to use authentication from Microsoft Entra ID.
 Click to enlarge.
Click to enlarge.
- When opening your instance, the normal login page will appear.
- Enter your credentials and the login page will automatically detect, based on your entered email domain, that you want to authenticate with Microsoft Entra ID. This is also indicated by it displaying SINGLE SIGN-ON ENABLED.

Click to enlarge.
- The login page will redirect you to your corporate login.
- You have now successfully integrated Microsoft Entra ID as SSO provider in PRTG.
Step 4: Invite Entra ID users
- You can now invite other users from your active directory into PRTG Hosted Monitor.
- Click the Setup button on your PRTG instance.
 Click to enlarge.
Click to enlarge.
- Select User Accounts.
 Click to enlarge.
Click to enlarge.
- Click on Invite User.
 Click to enlarge.
Click to enlarge.
- Fill in the details, set Federated Directory User as Login Type and click Send Invite.
 Click to enlarge.
Click to enlarge.
What happens to already invited users?
Let's assume, that you have configured a Microsoft Entra ID integration for the email domain mycompany.com for your PPHM instance.
All existing accounts that have an '@mycompany.com' email address, will be switched automatically to Microsoft Entra ID authentication flow, when entering their email address next time in the login form. These accounts will only be able to log in through the Microsoft Entra ID authentication flow.
All invited users that do NOT have a mycompany.com email address, will be using the default authentication flow with the email address and password.
Error Handling
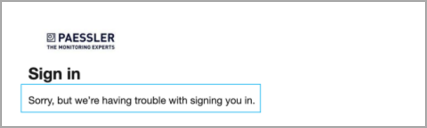
1. Incorrect Application ID.
If the user has used an invalid application ID , the following message is shown. The user must use the correct application ID connected to the Paessler Entra ID tenant.
2. CANNOT READ PROPERTY 'INDEXOF' OF UNDEFINED.
Email Address
This error occurs when the user tries to authenticate with Entra ID credentials that has no associated email address. To avoid this, an associated email address should be entered in the Contact Information section on their Entra ID portal.
3. FAILED TO OBTAIN ACCESS TOKEN.
This error can occur if the user enters the wrong client secret or if the client secret has expired.
Wrong Client Secret
The user has copied the secret ID from the Microsoft Entra ID portal instead of the value that contains the secret.
Expired Client Secret
The client secret has an expiration date. This is configured when the user is creating a client secret. We recommend that the user configures the expiration date to avoid errors.
Created on Apr 13, 2023 8:55:50 AM by
Yasodhara Das [Paessler Support]
Last change on Feb 7, 2025 8:23:34 AM by
Yasodhara Das [Paessler Support]





Add comment