We've started implementing Subject Alternative Name (SAN) SSL/TLS Certificates in our environment. I suspect the SSL Certificate Sensor isn't currently capable of differentiating the SAN Certificate alternative name from the SAN Certificate's Common Name and is therefore failing the sensor channel's CN check.
Is that a known issue, and if so, I'd like to recommend that it be considered for a road map item in the future.
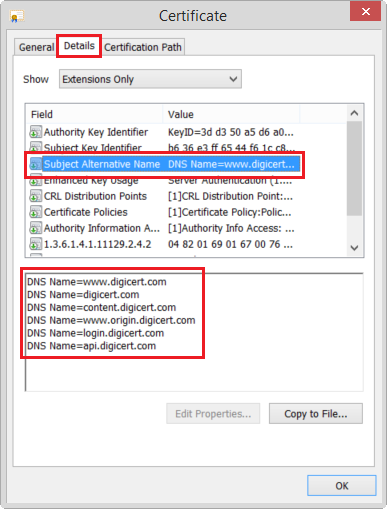
Otherwise, maybe you could point out what I might be doing wrong. All other online SSL Checker Websites are reading my common name check correctly.
Example: SAN Cerficiate's CN:
Thank You, Adam
Add comment