This article applies as of PRTG 23
Credentials for Microsoft 365 and permissions for Microsoft Graph
Before you can set up the Microsoft 365 Service Status sensor or the Microsoft 365 Service Status Advanced sensor, you need to define credentials for Microsoft 365 in the settings of a parent object.
The credentials you need are the Tenant ID, the Client ID, and the Client Secret. You obtain the credentials in the Microsoft Azure Portal. There you can also set the permission that the Microsoft 365 sensors require to read data from Microsoft Graph.
The following step-by-step guide shows you how to obtain the necessary credentials and how to set the required API permission.
Log in to the Microsoft Azure Portal and follow the steps below:
- Step 1: Get the client ID and the tenant ID
- Step 2: Get the client secret
- Step 3: Set the permission for Microsoft Graph
- Step 4: Authorize the new application (Admin consent required)
Step 1: Get the client ID and the tenant ID
Take the following steps to register your application with Microsoft Entra ID to be assigned a client ID. You can use either the Azure Portal or the Microsoft Entra admin portal. The only difference is how you navigate to App registrations:
Using the Azure Portal: Open Microsoft Entra ID in the Microsoft Azure Portal and go to the App registrations tab.
Using the Microsoft Entra admin center: Go to the App registrations tab under Applications.
- Click New registration to open the Register an application dialog.
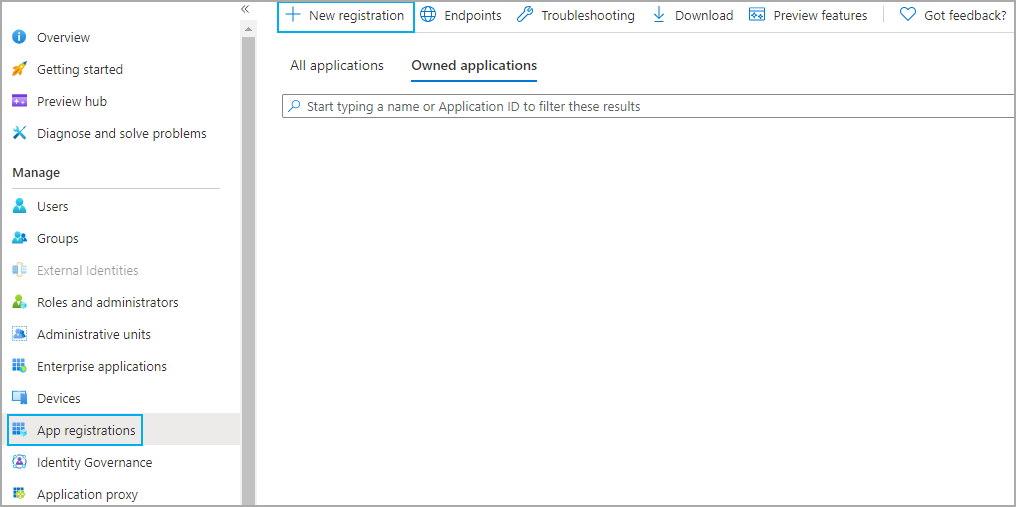
Click to enlarge.
- Enter a display name, for example, Microsoft 365 Service Status.
- Leave all other settings as they are.
- Enter the redirect URI where the authorization server sends you after the registration and authorization of the app. This is required for most authentication scenarios and can be specific for your setup. Note that there are specific rules for the redirect URI.
Note: Enter login.microsoftonline.com if you have no specific redirect URI.
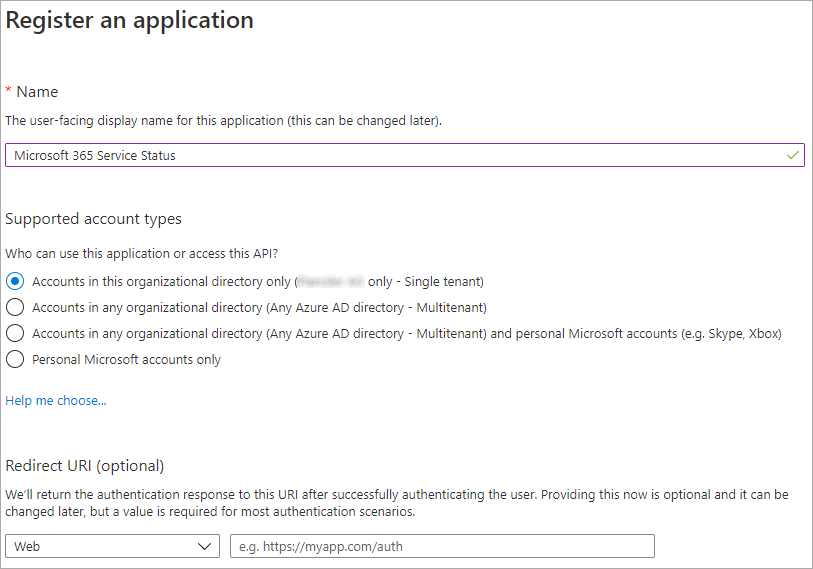
Click to enlarge.
- Click Register to register the new application.
- The Overview tab of the newly registered application opens.
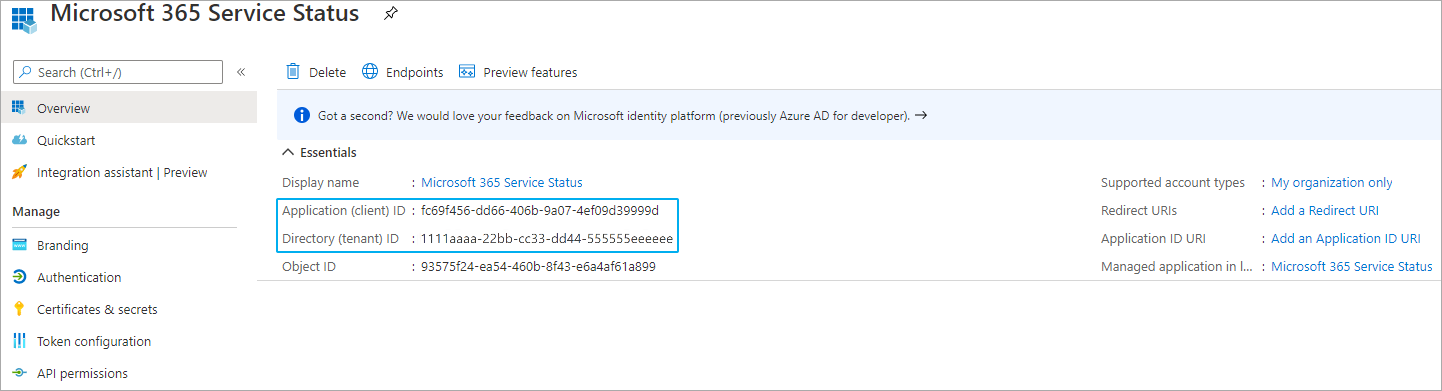
Click to enlarge.
- Copy the Application (client) ID and the Directory (tenant) ID and enter them in the credentials for Microsoft 365 section in the settings of the device, group, or probe in or on which you plan to add the sensors.
Step 2: Get the client secret
Take the following steps to create an application password, also known as client secret.
- Go to the Certificates & secrets tab.
- Click New client secret to open the Add a client secret dialog.
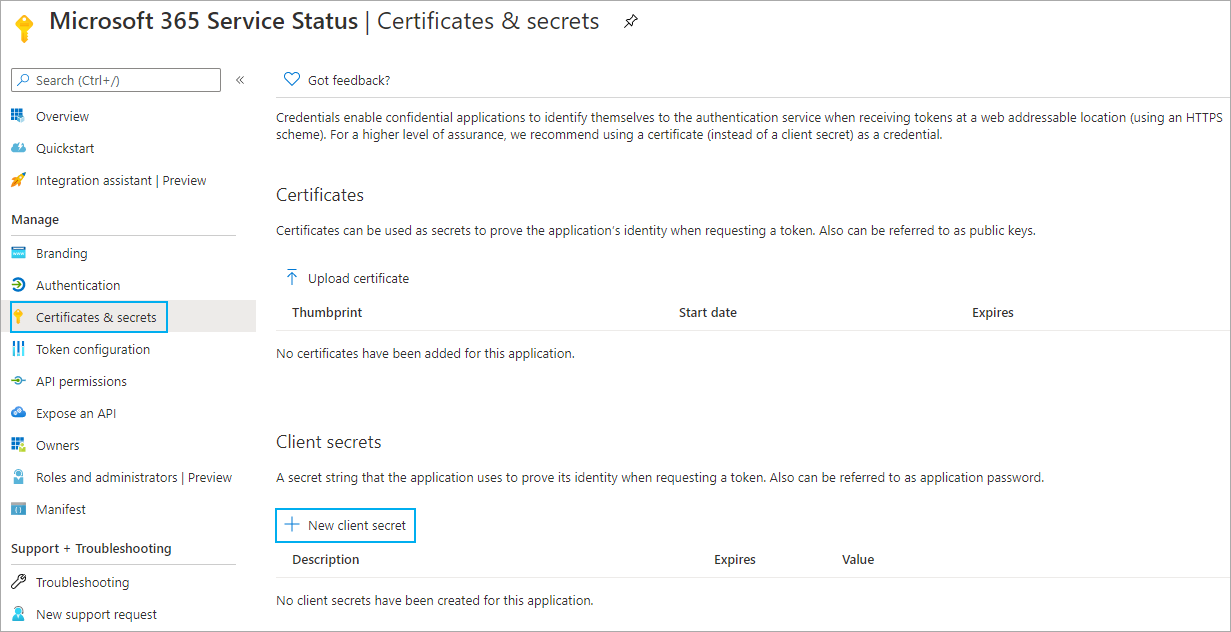
Click to enlarge.
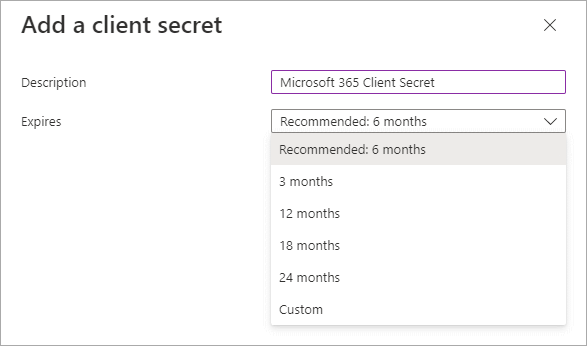
- Enter a Description, for example, Microsoft 365 Client Secret.
- Select a period after which the client secret expires.
Click to enlarge.
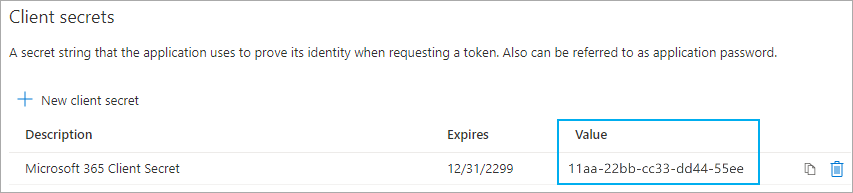
- Click Add to create and display the new client secret for your application.
Click to enlarge.
- Copy the client secret to enter it in the credentials for Microsoft 365 section of the object for which you already added the tenant ID and client ID.
| Important notice: Make sure that you directly copy the client secret after you created it. If you leave the page, the client secret is not shown anymore. You have to create a new client secret. |
Step 3: Set the permission for Microsoft Graph
Take the following steps to set the required permission for the Microsoft 365 sensors to be able to query data from Microsoft Graph.
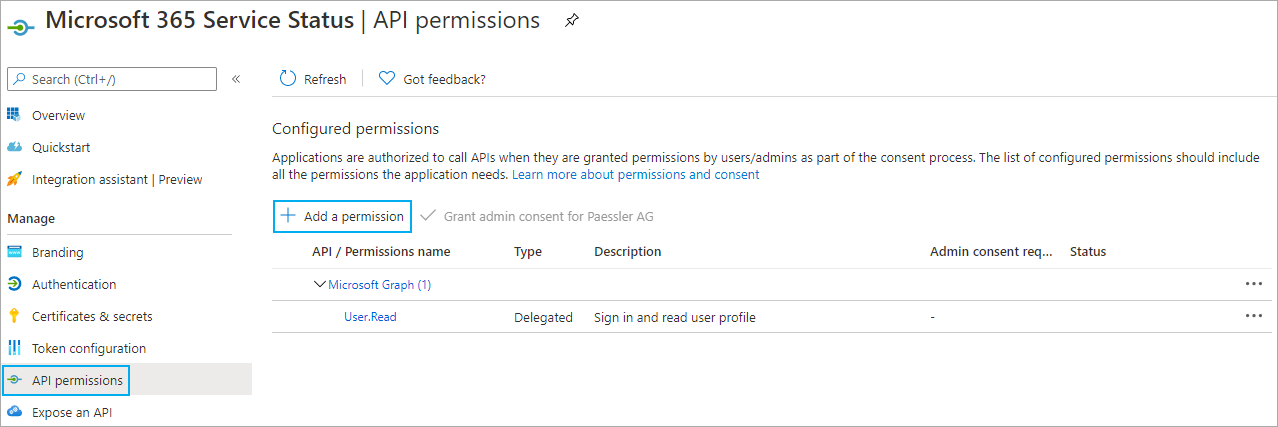
- Go to the API permissions tab.
- Click Add a permission to open the Request API permissions dialog.
Click to enlarge.
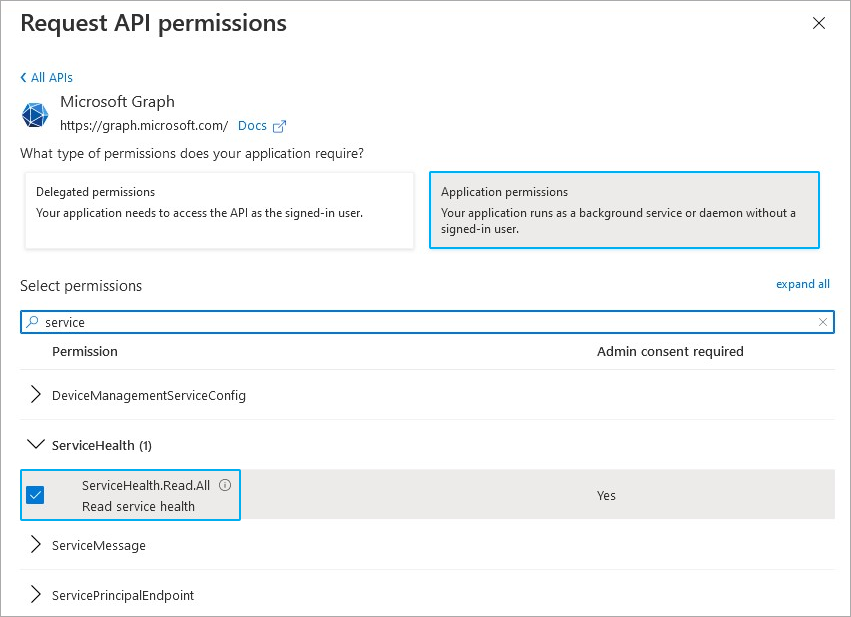
- Select the Microsoft Graph tile.
- Click Application permissions.
- Enter service in the search bar below Select permissions.
- Enable the check box next to ServiceHealth.Read.All.
- Click Add permissions to add the required permission.
Click to enlarge.
Step 4: Authorize the new application
Take the following steps to authorize the new application.
- Open the following URL
https://login.microsoftonline.com/your_tenant_ID/adminconsent?client_id=
{your_client_ID} and click Accept to accept the request.
- For your_tenant_ID, enter the tenant ID of the newly created application.
- For your_client_ID, enter the client ID of the newly created application.
- Note: You can find the Application (client) ID and the Directory (tenant) ID on the Overview tab of your newly created application.

Click to enlarge.
Note: It can take up to a few minutes until the authorization was processed.
You can now create the Microsoft 365 Service Status sensor and the Microsoft 365 Service Status Advanced sensor.
More








Add comment