Hi,
Not really a question, more as a quick howto as I didn't really find a guide on how to do this. This might not be the cleanest option there is, but this was all I had the budget for.
Background
We inherited an AWS tenant from a previous IT partner of our customer and needed to set up backups and monitoring for them. As we use PRTG a a single pane of glass regarding monitoring we didn't want to set up AWS notification mails etc.
Requirements
Make sure you've set u connection between PRTG and AWS using an access key using the following guide: https://kb.paessler.com/en/topic/38083-how-do-i-set-permissions-for-the-amazon-web-services-aws-api-key-to-use-certain-sensors-in-prtg
Set up AWS
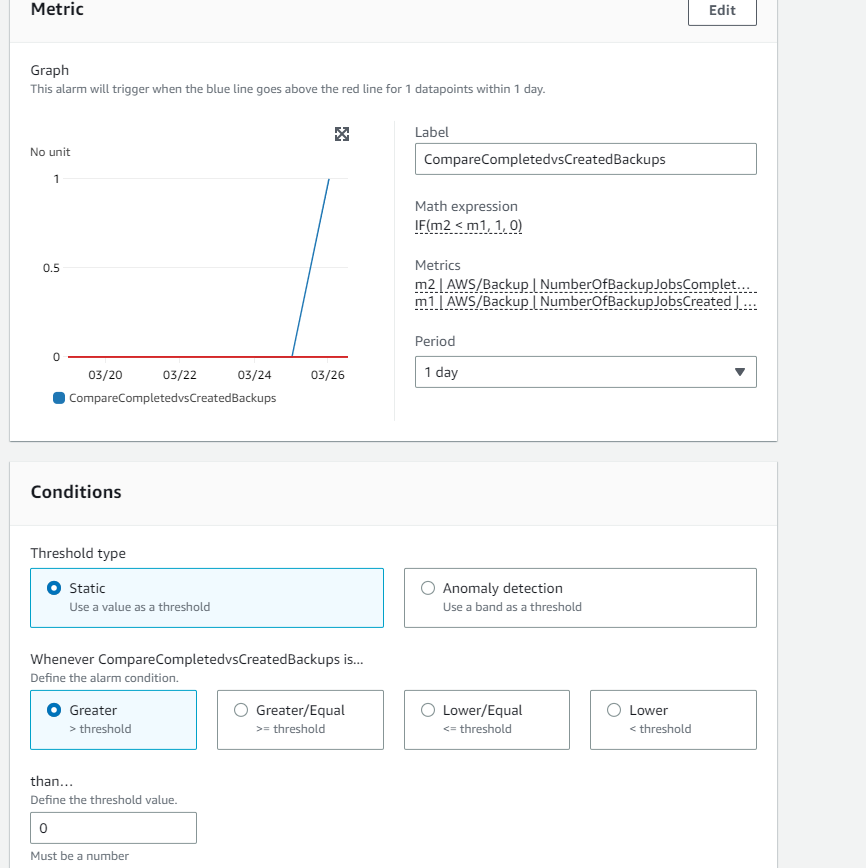
This will be done using alarms and metrics in AWS CloudWatch. We will count the number of backupjobs we configured and compare it to the amount of jobs that are completed in the last day.
In your AWS tenant, go to CloudWatch > Metrics. In the browse section, go to All > backup > By Backup vault (unless you want to split up monitoring per resourcetype e.t.c.) Select the NumberOfBackupJobsCreated and NumberOfBackupJobsCompleted.
In the Graphed metrics tab you'll see the 2 metrics you selected. Make sure you set these to SUM and over a period of 1 day.
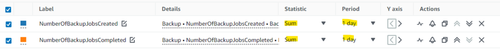
We will now also need to create an expression to compare these two.
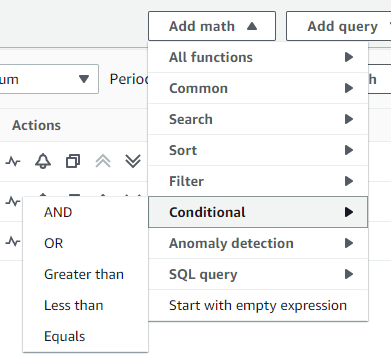
Using Add math > Conditional > less than we can compare the two metrics we selected earlier. Make sure these are correct.
In my example the expression IF(m2 < m1, 1, 0) translates to:
IF(Jobscompleted < Jobscreated, return "1", otherwise "0")
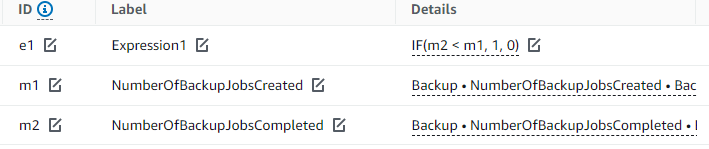
We will now create an alarm that throws an error if the value is one (AKA, jobs completed is lower than the existing jobs). You can do this straight from the same panel by pressing the bell under Actions.
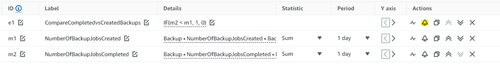
Create an alarm that goes into error if the expression is greater than 0 and give it a logical name.
Set up PRTG
In PRTG, make sure you have the AWS credentials filled in for the probe so the AWS sensors are available.
Create a new AWS Alarm sensor and check the alarm you just created. It should automatically go in error state when the alarm trips in AWS so no need to manually set any limits in the channels itself.