While PRTG doesn't offer built-in sensor for Meraki's devices our Custom Sensors can monitor most of the available information.
The built-in SNMP Traffic Sensor should also work but doesn't as Meraki's SNMP agent implementation does not respond to uptime queries.
There are two very distinct ways of querying Meraki devices, they can either be monitored via the cloud(dashboard) or directly (using the individual AP IP addresses). The information available using each method is distinct.
Meraki has an excellent SNMP Overview and Configuration article available at their website.
Option 1 - Monitor the Dashboard 'cloud'
Setup - Dashboard
Configuration steps as provided by Meraki:
| The Dashboard can be configured for SNMP polling from Organization > Settings > SNMP. Once SNMP has been enabled you will be able to send the SNMP requests to the host that is defined directly under the enable setting. It also defines the community string and provides a sample command to extract information via SNMP requests. |
Once enabled you'll be provided the required SNMP host and Credentials, for example:
| Host(The device's address within PRTG) | n7.meraki.com |
| SNMP Community | hasd6dsa |
| Port | 16100 |
Setup - PRTG
From there you can also download the MERAKI-CLOUD-CONTROLLER-MIB which will be useful later. Download the MIB file and copy it into "C:\Program Files (x86)\PRTG Network Monitor\MIB\".
You're also required to create a lookup file for the Device's State definition, please copy/paste the text below into an text file and save it as prtg.customlookups.meraki.devstatus.ovl under C:\Program Files (x86)\PRTG Network Monitor\lookups\custom\
<?xml version="1.0" encoding="UTF-8"?>
<ValueLookup id="prtg.customlookups.meraki.devstatus" desiredValue="1" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="PaeValueLookup.xsd">
<Lookups>
<SingleInt state="Ok" value="1">Online</SingleInt>
<SingleInt state="Error" value="0">Offline</SingleInt>
</Lookups>
</ValueLookup>
Restart PRTG's Core Server afterwards.
Creating sensors within PRTG
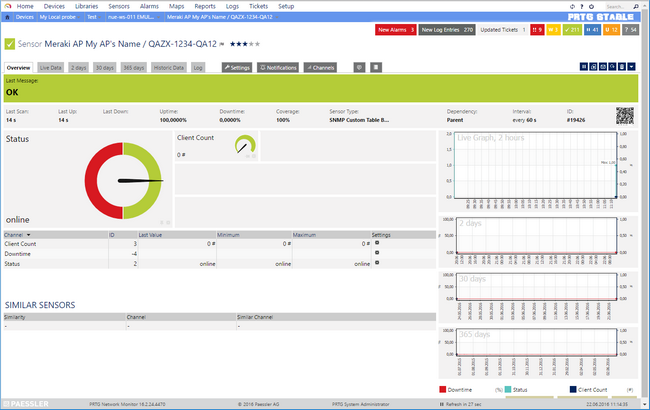
Once you've created a new device with the provided Address for SNMP Queries (e.g.: n7.meraki.com), configure it's SNMP Credentials (Version, Community and port) accordingly. Once the credentials are configured, add a new Sensor and search for the SNMP Custom Table Sensor.
During it's creation the Sensor will ask for the Table's OID, please enter 1.3.6.1.4.1.29671.1.1.4. PRTG will then render a table and display all information available on your controller (within the Dashboard's SNMP devTable). You'll have to use the top check-box to select all available access points. Additionally, please configure the following:
| Sensor Name | Meraki AP [rowidentifier] |
| Identification Column | devName |
| Sensor Channel #1 Name | State |
| Sensor Channel #1 Column | devStatus |
| Sensor Channel #1 Unit | Value Lookup |
| Sensor Channel #1 Value Lookup | prtg.customlookups.meraki.devstatus |
| Sensor Channel #2 | Enabled |
| Sensor Channel #2 Name | Connected Clients |
| Sensor Channel #2 Column | devClientCount |
| Sensor Channel #2 Unit | Count |
Press Continue, and PRTG will deploy a sensor for each available AP(Device), the primary channel (State) will tell you whenever the AP is connected or disconnected, when disconnected the sensor will go down. The secondary channel (Connected Clients) will display and graph the amount of clients connected to this Access Point.
Option 2 - Local device polling
Setup - Dashboard
Configuration steps as provided by Meraki:
| In this scenario the SNMP traffic would stay within the local network and each device would need to be polled from the network management system. These settings can be found under Network-wide > General > Reporting: |
| Using SNMP to directly poll individual devices provides the ability to choose between SNMP v1/v2c or v3. You will not be able to poll repeaters using SNMP as they do not have an IP address on the Local LAN |
| By default, Meraki devices cannot be polled from outside the network. However, after setting up the community string, an MX can be configured to allow polling from a remote IP whitelist, configured under Security appliance > Configure > Firewall & traffic shaping. |
Setup - PRTG
Within PRTG you'll need to make sure that you can reach each individual AP by It's IP Address, then create a new device for each AP you want to monitor directly, you'll also have to configure the SNMP Credentials accordingly.
Creating sensors within PRTG
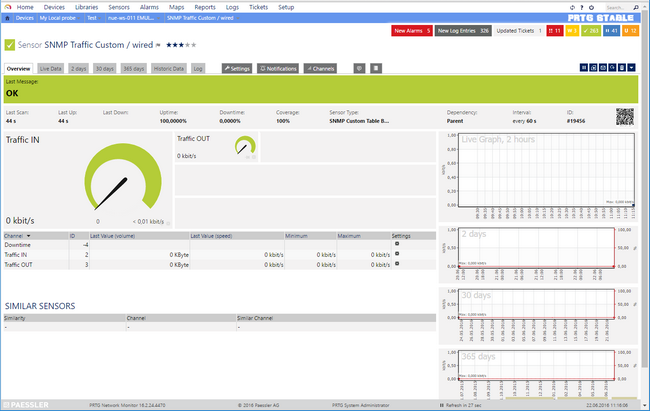
For each device that you've created within PRTG, add a new sensor, search for the SNMP Custom Table Sensor.
During it's creation the Sensor will ask for the Table's OID, please enter 1.3.6.1.2.1.31.1.1. PRTG will then render a table and display the available information contained in the SNMP Interfaces Table of the polled device. The available interfaces will be wired0, wifi0 and wifi1.
Select the desired interfaces from the list and configure the following:
| Sensor Name | SNMP Traffic [rowidentifier] |
| Identification Column | ifName |
| Sensor Channel #1 Name | Traffic IN |
| Sensor Channel #1 Column | ifHCInOctets |
| Sensor Channel #1 Value Type | Delta (Counter) |
| Sensor Channel #1 Unit | BytesBandwidth |
| Sensor Channel #2 Name | Traffic OUT |
| Sensor Channel #2 Column | ifHCOutOctets |
| Sensor Channel #2 Value Type | Delta (Counter) |
| Sensor Channel #3 Unit | BytesBandwidth |
Press Continue, and PRTG will deploy a Traffic Sensor for each selected interface, please note that the sensor will not support the same features as the standard SNMP Traffic Sensor but it should work as a workaround.
For further details:
http://blog.danielpark.com.au/2013/03/29/meraki-mib-cheat-sheet/
https://documentation.meraki.com/zGeneral_Administration/Monitoring_and_Reporting/SNMP_Overview_and_Configuration
https://kb.paessler.com/en/topic/59986-help-monitoring-meraki-network#reply-200811


Add comment